Author: Armen Gharibian, Desktop & Applications Architect 
I was recently asked to create a secondary password policy for a client. They were looking to enforce complex passwords for their end-users and wanted a way to test the new settings on a subset of users before making the change in the entire domain.
My initial thought was to simply create a new Group Policy Object (GPO) with the desired password requirements and target machines via security group or Organizational Unit (OU). After setting up the GPO and running some initial testing, I determined that the newly created password GPO was being applied, however the password complexity requirements were not taking effect. Instead, the Default Domain Policy password settings were still in effect.
With further research, I found that Microsoft Windows 2000 and 2003 Active Directory domains were only allowed one password policy, the default domain policy. Starting with Windows 2008 Active Directory domains, Microsoft introduced a feature called Fine-Grained Password Policies.
Fine-Grained Password Policies allow you to “…specify multiple password policies within a single domain. You can use fine-grained password policies to apply different restrictions for password and account lockout policies to different sets of users in a domain.” For example, an administrator can specify strict password policies for privileged IT and service accounts, while configuring less stringent policies for standard users. In short, with fine-grained password policies you can configure different requirements for specific users or security groups – just what I was after.
How to Implement Fine-Grained Password Polices
There are a few methods an administrator can use to implement fine-grained password polices depending on the operating system: Active Directory Service Interfaces (ADSI), LDAP Data Interchange Format (LDIF), Powershell, and a new Wizard (Server 2012)
Personally, I enjoy working with Powershell; I ran the following as a domain administrator using the Powershell Active Directory module to create the Fine-Grained Password Settings Objects (PSOs). In this case, the client wanted to require their users to set complex passwords containing a minimum of 8 characters. The current policy was requiring only 6 characters without any complexity enforced. The client also wanted to increase their password history count from 1 to 24.
Here is a taste of the Powershell command used to create the PSO:
New-ADFineGrainedPasswordPolicy -Name “ComplexPasswordPSO” -Precedence 500 -ComplexityEnabled $true -Description “Complex Password Policy”-DisplayName “Complex PSO” -LockoutDuration “0.00:30:00” -LockoutObservationWindow “0.00:30:00” -LockoutThreshold 6 -MaxPasswordAge “60.00:00:00” -MinPasswordAge “1.00:00:00” -MinPasswordLength 8 -PasswordHistoryCount 24 -ReversibleEncryptionEnabled $false
Once my PSO was created, I used Powershell to deploy it to the IT Admins security group for testing:
Add-ADFineGrainedPasswordPolicySubject ComplexPasswordPSO -Subjects ‘IT Admins’
Note: you need to supply the name of your PSO and subjects. The subject’s field can be single users or a security group
Should you need to modify your PSO post deployment, you can do so by using the following:
Set-ADFineGrainedPasswordPolicy “ComplexPasswordPSO” -MinPasswordLength 10 -PasswordHistoryCount 30
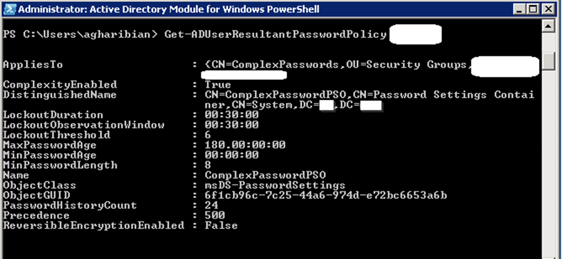
I also used the following command to verify settings on a single user in the Security Group:
Get-ADUserResultantPasswordPolicy Username
Conclusion:
Multiple, granular, highly targetable, password policies can be created in a domain by using fine-grained password policies. This allows an administrator to create heightened security policies for certain user groups. It also allows for testing password policies before changing them for the entire domain. A caveat to fine-grained password policies: the domain level needs to be Server 2008 and above.
For more information refer to the following Microsoft article:
https://technet.microsoft.com/en-us/library/cc770394%28v=ws.10%29.aspx
Armen Gharibian, Desktop and Applications Architect – Armen is an IT professional with more than 8 years of systems management and technical support experience. He has expertise in information technologies, ranging from hardware and software to system security and networking with a strong emphasis on the Microsoft Systems Center Configuration Manger and Operations Manager. For more information, please contact agharibian@helient.com.


